Security Implementation
Looking beyond administrative measures (in the form of security documentation), the focus is on comprehensively rolling out technical and organisational measures adapted to the customer’s corporate culture. Customers can take their pick of services guaranteeing the implementation of an information security management system complying with the requirements of ISO/IEC 27001, cybersecurity consistent with relevant legislation, and/or the preparation of their information system for certification up to the “Secret” classification level.
The target customer groups are state administration institutions, large and medium-sized companies, and anyone bidding for government contracts.
Information security management system at an organisation
An information security management system is implemented at an organisation by applying procedural and technological measures complying with the requirements of ČSN ISO/IEC 27001. The overarching objective is to devise a system for the efficient establishment, integration, operation, monitoring, review, maintenance and improvement of the information security system at an organisation. It consists of sets of security policies, procedures, directives and relevant resources and activities managed by the organisation to safeguard the protection of assets.
Service parameters
- Analysis of the current information security situation
- Recommendation of the scope to be covered by security policy
- Planning and introduction of arrangements for the organisation of information security
- Risk analysis, including the creation of a risk register
- Draft statement of applicability
- Drafting and implementation of technical measures
- Drafting of relevant security documentation
- Optional arrangements for full compliance with ČSN ISO/IEC 27001
- Consultation arrangements
Key benefits
- Enhanced credibility
- Efficient management of security incidents
Cybersecurity Act
The Cybersecurity Act governs the rights and obligations of natural and legal persons, the competence and authority of public authorities, and their cooperation with each other in the domain of cybersecurity. The service makes sure that cybersecurity at an organisation is consistent with the law. It entails the drafting and implementation of organisational and technical measures. Organisational measures mainly comprise risk management and a definition of the procedural security documentation. Technical measures, on the other hand, concentrate on physical, communication and information security.
Service parameters
- Analysis of the current situation
- Recommendation of the scope of application
- Drafting of security policy
- Draft methodology for asset and risk identification and appraisal
- Drafting of an evaluation report
- Draft statement of applicability
- Draft risk management plan
- Draft security awareness development plan
- Proposal for the management of cybersecurity incidents
- Draft strategy for business continuity management
- Drafting and implementation of the requisite technical measures
Key benefits
- Guarantee of organisational compliance with the Cybersecurity Act
- Experienced team of security experts
Act on the Protection of Classified Information
The Act on the Protection of Classified Information governs principles for defining classified information, conditions of access thereto, and other requirements for the protection thereof. It also regulates principles for determining sensitive activities and conditions for the performance thereof. The main objective is to prime the customer’s information system for certification so that information up to the “Secret” classification level can be processed. Under the service, design and operational documentation is drafted and technical measures are planned and implemented.
Service parameters
- Drafting of security policy and the outcome of the risk analysis
- Recommendation of information system security
- Drafting of a set of information system security tests, a description thereof, and a description of the results of testing
- Drafting of operational security documentation for the information system
- Draft description of the security of the development environment
- Production of a physical security project
- Drafting and implementation of technical measures
- Consultation arrangements
Key benefits
- Complete preparation of the information system for certification
- Possibility of processing classified information up to and including the “Secret” level
Information Security Services
They also pave the way for a system to be devised for the efficient management of security, with stress on the clearly defined responsibilities and obligations of employees. Customers are free to combine any services in the fields of security analysis and security documentation in line with the particular requirements of their organisation.The target customer groups are central and local government authorities, local internet service providers and large and medium-sized companies.
Security Analysis
The overarching objective of a security analysis is to identify how secure information at an organisation currently is. In particular, an analysis determines the risks to which an organisation is susceptible and recommends measures that will either eliminate them or reduce them to an acceptable level.
Security Situation Ascertainment
Security situation ascertainment is a fundamental tool for the independent evaluation of the level of security at an organisation. It identifies and determines the current level of information security at the customer, taking account of security measures that are already in place.
Service Specifications
- Basic independent assessment of the level of the customer’s information security
- Definition of basic measures to be taken in response to the identified risks
- List of simple project plans to eliminate identified risks
- Measures recommended to eliminate identified risks
- Consultation arrangements
Key Benefits
- An independent evaluation of the information security situation, the identification of risks posed to the organisation and measures recommended for their elimination.
Risk Analysis
An advanced security method for the systematic identification of the risks to which an organisation is exposed. It determines primary and secondary assets and, by tracing the links between them, is able to deduce the danger posed by the various risks. It is a useful tool for customers when they are considering the effectiveness of investing resources in security.
Service Specifications
- Recommendation of the scope of application of risk analysis, risk identification, and determination of the risk level
- Organisational and technical measures recommended for selected risks
- Creation of project plans to eliminate selected risks
- Risk management setup
- Consultation arrangements
Key Benefits
- An independent evaluation of the information security situation, the identification of risks posed to the organisation and measures recommended for their elimination.
Security Documentation
Security documentation primarily focuses on organisational measures, ranging from the most senior management level to the actual implementing procedures that are to be applied. It defines basic information security rules and procedures in response to procedural, technical and staffing requirements throughout an organisation, with due regard for the culture that has been cultivated here. The main objective is to clearly define the responsibilities of employees across the organisation and to form a basis for the effective implementation and management of information security at an organisation.
Service Specifications
- Information security strategy
- Management documentation defining the basic security rules at a large organisation
- The security policy at the organisation
- Security manuals for users, administrators, security managers, etc.
- Security procedures under individual measures
- Consultation arrangements
Key Benefits
- Establishment of a security strategy at the organisation
- Establishment of clear responsibilities and obligations for employees
- Security rules and procedures recommended at the organisation

Relevant Products and Services
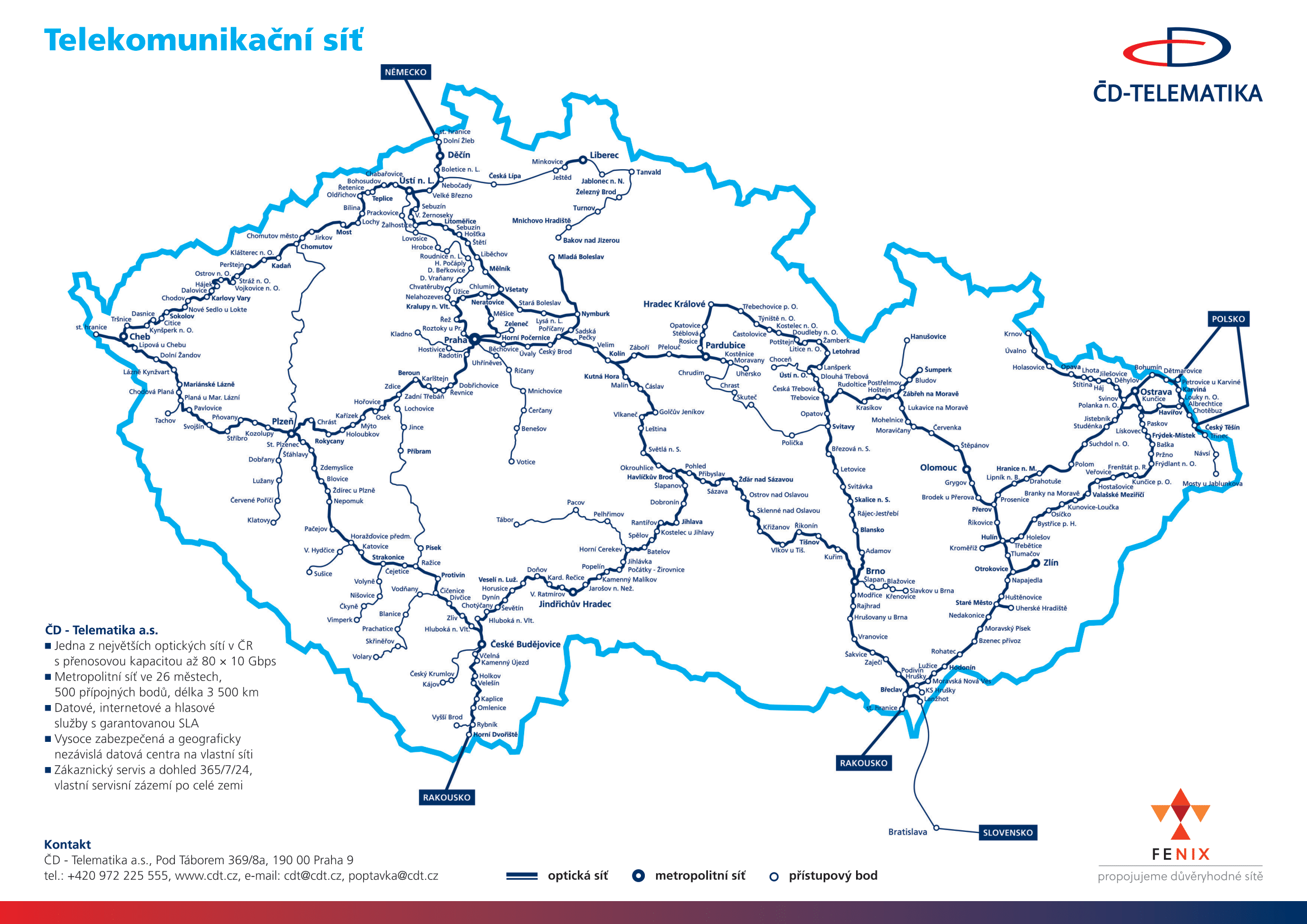
ICT Services
Use our indepent datacentre for serverhousing
Internet
The CDT-Internet service enables access to the Internet via the ČD - Telematika network